1. What makes a firewall a good security investment? Accessing the Internet, find two or three firewall vendors. Do they provide hardware, software or both?
Elias (2003) described that firewall acts as a sheild to prevent data and information inside the network to the public. Firewall is a hardware and software tool defines control and access of network and computers.
Firewall vendors:
Check Point Firewall
It is a security vendor, it sells hardware appliance and software firewall.
Kerio Technologies
It is a security vendor, it sells software firewall only.
Comodo
It is a security vendor, it sells software firewall and integrated security solutions.
2. Find out if your university or workplace has a backup policy in place. Is it followed and enforced?
In my workplace, there is a backup policy for the main servers. It is a enforced policy. In the policy, all files and data are backup daily to the backup server. As the backup server uses hard drives to store data, RAID-5 system is used and the backup server is located away from the main servers.
A tape backup system is also implemented to some of the servers. It backup data in a full backup manner. The tapes are rotated and changed every two weeks and the tape with the data is stored away from the server and tape backup system.
3. Most of the antivirus software perform an active scanning of the user activity on the Internet, detecting downloads and attachments in e-mails. Hackers have readily available resources to create new viruses. How easy is it to find a virus writing kit? Search the Internet and find such a tool. For example, see what you can find at http://vx.netlux.org/dat/vct.shtml.
In the http://vx.netlux.org, the virus can be easily generated with the generator.
Each of them generate different kind of virus.
As I searched with keyword "create computer virus", I found a blog from Bendib (Nov 22, 2008. 6:35 PM) posted a virus source code in his blog.
As I search again in Google with keyword "computer virus generator", one of the computer security website shows the name of the generator. I then search again with the name listed in the security website. It is easy to find the generator with the search engines.
Monday, April 27, 2009
Exercise 14: Electronic payments and security II
1. What are cookies and how are they used to improve security?
As the web pages from the web servers are stateless, cookies is developed to store the information in users' computer for maintaining the interaction between the web page changes within a website and revisit of the web site by user. (W3.org)
According to W3.org, there is a attribute in cookies. The attribute validates the information send and through from the users' browser to the originating server/website but not others, this mechanism prevents the information in cookies not to be collected by others.
2. Can the use of cookies be a security risk?
The common information contained in cookies are:
a. the session ID or authorization information
b. issue time and date of the cookie
c. time of expiration
d. the IP address of the browser the cookie was issued to
e. a message authenticity check (MAC) code
Although the mechanism prevents the information send to other servers, there is still security risk when browsing the websites. The adverising agent in the internet promote the website holder to post advertisement in their website. As a result, when a user browse the website which subscribe the agent, the information will be logged in their cookies. The collected information in the cookies with the IP address contained can be used to analyze for the user habbits and interests. The privacy of the user is affected.
Reference:
Lincoln D. S., John N. S. (2003), The World Wide Web Security FAQ, Retrieved 27 April 2009 from http://www.w3.org/Security/Faq/wwwsf2.html
As the web pages from the web servers are stateless, cookies is developed to store the information in users' computer for maintaining the interaction between the web page changes within a website and revisit of the web site by user. (W3.org)
According to W3.org, there is a attribute in cookies. The attribute validates the information send and through from the users' browser to the originating server/website but not others, this mechanism prevents the information in cookies not to be collected by others.
2. Can the use of cookies be a security risk?
The common information contained in cookies are:
a. the session ID or authorization information
b. issue time and date of the cookie
c. time of expiration
d. the IP address of the browser the cookie was issued to
e. a message authenticity check (MAC) code
Although the mechanism prevents the information send to other servers, there is still security risk when browsing the websites. The adverising agent in the internet promote the website holder to post advertisement in their website. As a result, when a user browse the website which subscribe the agent, the information will be logged in their cookies. The collected information in the cookies with the IP address contained can be used to analyze for the user habbits and interests. The privacy of the user is affected.
Reference:
Lincoln D. S., John N. S. (2003), The World Wide Web Security FAQ, Retrieved 27 April 2009 from http://www.w3.org/Security/Faq/wwwsf2.html
Exercise 13: Electronic payments and security I
1. List and describe your experiences with a secure Web site. Some examples may be:
• University enrolment;
• online banking, auctions, real estate;
• booking a cheap air ticket or concert ticket;
• shopping online for a book, software or a CD.
I have tried to apply jobs with the secure website. The website is established by the Hong Kong government with Hong Kong University. The sys tem is named Government Vacancies Enquiry System .
When I enter the application form at the site, a lock liked symbol is located on the status bar of the browser. The system does not allow to use the forward and backward button on the browser to go back or forth. Changes can be made by selecting the page before the end of entering information.
Finally, a agreement is to be signed by selecting the check box and press SUBMIT button to send the form.
2. What is SET and how does it compare to SSL as a platform for secure electronic
transaction? Is SET in common use?
Based on the Bernstein, Bhimani, Schultz, Siegel (1996), In term of protocol the SSL is a general purpose protocol between browser and server while SET is a special protocol to link up between customer, merchant, card issuing bank and merchant’s bank.
Interm of keys and signatures, SSL uses a pair of keys for encryption and digital signature but SET uses two pairs of keys for separating encryption and digital signature.
The SET is not a common use protocol becsue it only works with credit/debit card.
Reference:
Bernstein T., Bhimani A. B., Schultz E., Siegel C. A. (1996), Internet Security for Business, Wiley, p.332-351
• University enrolment;
• online banking, auctions, real estate;
• booking a cheap air ticket or concert ticket;
• shopping online for a book, software or a CD.
I have tried to apply jobs with the secure website. The website is established by the Hong Kong government with Hong Kong University. The sys tem is named Government Vacancies Enquiry System .
When I enter the application form at the site, a lock liked symbol is located on the status bar of the browser. The system does not allow to use the forward and backward button on the browser to go back or forth. Changes can be made by selecting the page before the end of entering information.
Finally, a agreement is to be signed by selecting the check box and press SUBMIT button to send the form.
2. What is SET and how does it compare to SSL as a platform for secure electronic
transaction? Is SET in common use?
Based on the Bernstein, Bhimani, Schultz, Siegel (1996), In term of protocol the SSL is a general purpose protocol between browser and server while SET is a special protocol to link up between customer, merchant, card issuing bank and merchant’s bank.
Interm of keys and signatures, SSL uses a pair of keys for encryption and digital signature but SET uses two pairs of keys for separating encryption and digital signature.
The SET is not a common use protocol becsue it only works with credit/debit card.
Reference:
Bernstein T., Bhimani A. B., Schultz E., Siegel C. A. (1996), Internet Security for Business, Wiley, p.332-351
Exercise 12: Designing for a secure framework
1. Find out about SET and the use of RSA 128-bit encryption for e-commerce.
SET stands for Secure Electronic Transaction. It is a protocol designed for secure credit and debit card transaction between customers and merchants. With this protocol, all messages including ordering and payment information are encrypted. As both parties using SET requires digital certificate, any modification of the data and information can be altered. As the merchants complete the transaction with the bank but not the customer directly, the privacy of customer is retained.
RSA 128-bit encryption is a encryption method for symmertic keys for the certificate issued to merchants and clients who uses SET for transactions.
RSA recommended that the 128-bits as a minimum symmetric security level till 2013 and beyond. This level requires the minimum RSA key size to be at 3072bits.
2. What can you find out about network and host-based intrusion detection systems?
Wikipedia (2009) stated that "A network intrusion detection system (NIDS) is an independent platform which identifies intrusions by examining network traffic and monitors multiple hosts. Network Intrusion Detection Systems gain access to network traffic by connecting to a hub, network switch configured for port mirroring, or network tap. An example of a NIDS is Snort."
It is found to be a packet level analyzer for intrusion.
Wikipedia (2009) stated that "A host-based intrusion detection system (HIDS) consists of an agent on a host which identifies intrusions by analyzing system calls, application logs, file-system modifications (binaries, password files, capability/acl databases) and other host activities and state. An example of a HIDS is OSSEC."
It is found to be a application level analyzer for intrusion.
3. What is ‘phishing’?
Phishing is a kind of technique to collect victim's user name and password for criminal activities.
It always uses emails that pretent itself as an enterprise or organization and send to the users. The email mostly used to acknowledge the user to change his/her password with a specified web address that similar to the real address.
When user click on the web address provided by that email, it leads the user to a fake website, which look and feel as the real website to collect the personal information such as user name and password of a bank account. It usually lead financial loss on victim user. (webopedia, Wikipedia)
Reference:
Wikipedia (2009), Intrusion detection system, Retrieved 24 May 2009 from http://en.wikipedia.org/wiki/Intrusion-detection_system
Wikipedia (n.d.), Phishing, Retrieved 28 April 2009 from http://en.wikipedia.org/wiki/Intrusion-detection_system
webopedia (n.d.), All About Phishing, Retrieved 28 April 2009 from http://www.webopedia.com/DidYouKnow/Internet/2005/phishing.asp
Secure Electronic Transaction (SET), Retrieved 4 May 2009 from http://lyle.smu.edu/~nair/courses/7349/SET.ppt
SET stands for Secure Electronic Transaction. It is a protocol designed for secure credit and debit card transaction between customers and merchants. With this protocol, all messages including ordering and payment information are encrypted. As both parties using SET requires digital certificate, any modification of the data and information can be altered. As the merchants complete the transaction with the bank but not the customer directly, the privacy of customer is retained.
RSA 128-bit encryption is a encryption method for symmertic keys for the certificate issued to merchants and clients who uses SET for transactions.
RSA recommended that the 128-bits as a minimum symmetric security level till 2013 and beyond. This level requires the minimum RSA key size to be at 3072bits.
2. What can you find out about network and host-based intrusion detection systems?
Wikipedia (2009) stated that "A network intrusion detection system (NIDS) is an independent platform which identifies intrusions by examining network traffic and monitors multiple hosts. Network Intrusion Detection Systems gain access to network traffic by connecting to a hub, network switch configured for port mirroring, or network tap. An example of a NIDS is Snort."
It is found to be a packet level analyzer for intrusion.
Wikipedia (2009) stated that "A host-based intrusion detection system (HIDS) consists of an agent on a host which identifies intrusions by analyzing system calls, application logs, file-system modifications (binaries, password files, capability/acl databases) and other host activities and state. An example of a HIDS is OSSEC."
It is found to be a application level analyzer for intrusion.
3. What is ‘phishing’?
Phishing is a kind of technique to collect victim's user name and password for criminal activities.
It always uses emails that pretent itself as an enterprise or organization and send to the users. The email mostly used to acknowledge the user to change his/her password with a specified web address that similar to the real address.
When user click on the web address provided by that email, it leads the user to a fake website, which look and feel as the real website to collect the personal information such as user name and password of a bank account. It usually lead financial loss on victim user. (webopedia, Wikipedia)
Reference:
Wikipedia (2009), Intrusion detection system, Retrieved 24 May 2009 from http://en.wikipedia.org/wiki/Intrusion-detection_system
Wikipedia (n.d.), Phishing, Retrieved 28 April 2009 from http://en.wikipedia.org/wiki/Intrusion-detection_system
webopedia (n.d.), All About Phishing, Retrieved 28 April 2009 from http://www.webopedia.com/DidYouKnow/Internet/2005/phishing.asp
Secure Electronic Transaction (SET), Retrieved 4 May 2009 from http://lyle.smu.edu/~nair/courses/7349/SET.ppt
Wednesday, April 15, 2009
Asking and Answering
This is asking and answering section, lets discuss the problems on the exercises and workshops!
Evaluation Report 1
Script is finished, Audio file prepared.
Fail to put into MS Word for upload.
I uploaded MP3 formatted file to EAST instead.
Evaluation Report also can be accessed with Sky Drive:
http://cid-df4d3bf95db02d9e.skydrive.live.com/browse.aspx/.Public?lc=1033
Fail to put into MS Word for upload.
I uploaded MP3 formatted file to EAST instead.
Evaluation Report also can be accessed with Sky Drive:
http://cid-df4d3bf95db02d9e.skydrive.live.com/browse.aspx/.Public?lc=1033
Tuesday, April 14, 2009
Workshop 0: Developer ot Project manager decision
I have decision to be a developer on the project team.
Monday, April 13, 2009
Workshop 3: Online Taxi Booking System: MySQL and Database design
a. Create passengers table

b. Structure of the table passengers

c. Create data 1

d. Create data 2

e. Read

f. Update

g. Destroy

1. Set up the MySQL tools

2. Rails will setup a new application directory for each of your web application projects.

3. One Rails is running you at http://localhost:3000, you need to configure database access. Connect to the database is specified in the config/database.yml file.

MySQL GUI connection settings

MySQL Administror window

Run select SQL command in MySQL GUI


b. Structure of the table passengers

c. Create data 1

d. Create data 2

e. Read

f. Update

g. Destroy

1. Set up the MySQL tools

2. Rails will setup a new application directory for each of your web application projects.

3. One Rails is running you at http://localhost:3000, you need to configure database access. Connect to the database is specified in the config/database.yml file.

MySQL GUI connection settings

MySQL Administror window

Run select SQL command in MySQL GUI

Workshop 4: Riding the Rails with Ruby
To do:
1. Spend some time moving your way through the 46 Ruby coding examples in the Ruby tutorial with code from http://www.fincher.org/tips/Languages/Ruby/
In this website, there are a lot of example for coding with Ruby.
2. What are the syntax difference in the way that Ruby and Javascript use the if statement?
In Javascript, the syntax of the if statement is as follows:
if (condition)
{
code to be executed if condition is true
}
else
{
code to be executed if condition is not true
}
Example:
if (time<10)
{
document.write("Good morning");
}
or
if (time==11)
{
document.write("Lunch-time!");
}
or
if(visitor == "teacher"){
document.write("My dog ate my homework...");
}else if(visitor == "principal"){
document.write("What stink bombs?");
} else {
document.write("How do you do?");
}
In Ruby, the if statement is as follow:
if( x < 7 && x > 12 ) { ... }
or
if x.between?(7,12) do ...
or
if income < 10000
rate = 0.02
elsif income < 30000
rate = 0.28
else
rate = 0.5
end
The else if used in the Javascript, in Ruby, it uses elsif. The Ruby language does not requires to user {} mark in beginning and the end of the if statement. There is no function x.between?(7, 12) in Javascript.
3. While Ruby and Python are quite similar, can you find some similarities between Ruby and Javascript?
Both Ruby and Javascript are requiring interpeter to run. Both are object-oriented.
Both language like C++ and Java.
Challenge Problems:
1. Create, test and debug a Ruby program called dognames.rb or catnames.rb to accept 3 names from the keyboard and to display each name on the screen in alphabetical order WITHOUT using a data structure such as a list.
Code of the dognames.rb
def dognames
puts "Enter first dog name : "
name1 = gets
puts "Enter second dog name : "
name2 = gets
puts "Enter third dog name : "
name3 = gets
myarray=[name1,name2,name3]
puts "Sorted dogs names:"
print "First dog is ", myarray.sort[0]
print "Second dog is ", myarray.sort[1]
print "Third dog is ", myarray.sort[2]
end
dognames
2. Write a Ruby program called fizzbuzz.rb that prints the numbers from 1 to 100. But for multiples of three print "Fizz" instead of the number and for the multiples of five print "Buzz". For numbers which are multiples of both three and five print "FizzBuzz".
Code:
def fizzbuzz
1.upto(100) do |temp|
if temp % 5 == 0 and temp % 3 == 0
puts "FizzBuzz"
elsif temp % 5 == 0
puts "Buzz"
elsif temp % 3 == 0
puts "Fizz"
else
puts temp
end
end
end
fizzbuzz
Result:
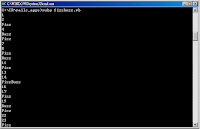
3. Compare the Ruby and Python versions of the dog years calculator:
#!/usr/bin/ruby
# The Dog year calculator program called dogyears.rb
def dogyears
# get the original age
puts “Enter your age (in human years): "
age = gets # gets is a method for input from keyboard
puts # is a method or operator for screen output
#do some range checking, then print result
if age < 0
puts "Negative age?!? I don't think so."
elsif age < 3 or age > 110
puts "Frankly, I don't believe you."
else
puts "That's", age*7, "in dog years."
end
dogyears
Python
#!/usr/bin/python
# The Dog year calculator program called dogyears.py
def dogyears():
# get the original age
age = input("Enter your age (in human years): ")
print # print a blank line
# do some range checking, then print result
if age < 0:
print "Negative age?!? I don't think so."
elif age < 3 or age > 110:
print "Frankly, I don't believe you."
else:
print "That's", age*7, "in dog years."
### pause for Return key (so window doesn't disappear)
raw_input('press Return>')
def main():
dogyears()
main()
By comparing both program,
a. The Python version is longer than the Ruby version.
b. The Ruby version does not require to define the main program to call the routine.
c. It is required to provide a mechanism to pause the program to hold teh result in Python while Ruby is not.
d. There is no function parameter required in Ruby program.
e. Line break or no line break output are different reserved word (puts, print) in Ruby.
Reference:
Ruby Tutorial with Code Samples (n.d.), http://www.fincher.org/tips/Languages/Ruby/
Selina D’S. (n.d.), T New Product Development with Ruby on Rails, Retrieve 10 April 2009 from www.aspiresys.com/WhitePapers/whitepaper_new_product_development-RoR_paper.pdf
w3school (2009), JavaScript If...Else Statements, Retrieve 10 April 2009 from http://www.w3schools.com/JS/js_if_else.asp
1. Spend some time moving your way through the 46 Ruby coding examples in the Ruby tutorial with code from http://www.fincher.org/tips/Languages/Ruby/
In this website, there are a lot of example for coding with Ruby.
2. What are the syntax difference in the way that Ruby and Javascript use the if statement?
In Javascript, the syntax of the if statement is as follows:
if (condition)
{
code to be executed if condition is true
}
else
{
code to be executed if condition is not true
}
Example:
if (time<10)
{
document.write("Good morning");
}
or
if (time==11)
{
document.write("Lunch-time!");
}
or
if(visitor == "teacher"){
document.write("My dog ate my homework...");
}else if(visitor == "principal"){
document.write("What stink bombs?");
} else {
document.write("How do you do?");
}
In Ruby, the if statement is as follow:
if( x < 7 && x > 12 ) { ... }
or
if x.between?(7,12) do ...
or
if income < 10000
rate = 0.02
elsif income < 30000
rate = 0.28
else
rate = 0.5
end
The else if used in the Javascript, in Ruby, it uses elsif. The Ruby language does not requires to user {} mark in beginning and the end of the if statement. There is no function x.between?(7, 12) in Javascript.
3. While Ruby and Python are quite similar, can you find some similarities between Ruby and Javascript?
Both Ruby and Javascript are requiring interpeter to run. Both are object-oriented.
Both language like C++ and Java.
Challenge Problems:
1. Create, test and debug a Ruby program called dognames.rb or catnames.rb to accept 3 names from the keyboard and to display each name on the screen in alphabetical order WITHOUT using a data structure such as a list.
Code of the dognames.rb
def dognames
puts "Enter first dog name : "
name1 = gets
puts "Enter second dog name : "
name2 = gets
puts "Enter third dog name : "
name3 = gets
myarray=[name1,name2,name3]
puts "Sorted dogs names:"
print "First dog is ", myarray.sort[0]
print "Second dog is ", myarray.sort[1]
print "Third dog is ", myarray.sort[2]
end
dognames
2. Write a Ruby program called fizzbuzz.rb that prints the numbers from 1 to 100. But for multiples of three print "Fizz" instead of the number and for the multiples of five print "Buzz". For numbers which are multiples of both three and five print "FizzBuzz".
Code:
def fizzbuzz
1.upto(100) do |temp|
if temp % 5 == 0 and temp % 3 == 0
puts "FizzBuzz"
elsif temp % 5 == 0
puts "Buzz"
elsif temp % 3 == 0
puts "Fizz"
else
puts temp
end
end
end
fizzbuzz
Result:

3. Compare the Ruby and Python versions of the dog years calculator:
#!/usr/bin/ruby
# The Dog year calculator program called dogyears.rb
def dogyears
# get the original age
puts “Enter your age (in human years): "
age = gets # gets is a method for input from keyboard
puts # is a method or operator for screen output
#do some range checking, then print result
if age < 0
puts "Negative age?!? I don't think so."
elsif age < 3 or age > 110
puts "Frankly, I don't believe you."
else
puts "That's", age*7, "in dog years."
end
dogyears
Python
#!/usr/bin/python
# The Dog year calculator program called dogyears.py
def dogyears():
# get the original age
age = input("Enter your age (in human years): ")
print # print a blank line
# do some range checking, then print result
if age < 0:
print "Negative age?!? I don't think so."
elif age < 3 or age > 110:
print "Frankly, I don't believe you."
else:
print "That's", age*7, "in dog years."
### pause for Return key (so window doesn't disappear)
raw_input('press Return>')
def main():
dogyears()
main()
By comparing both program,
a. The Python version is longer than the Ruby version.
b. The Ruby version does not require to define the main program to call the routine.
c. It is required to provide a mechanism to pause the program to hold teh result in Python while Ruby is not.
d. There is no function parameter required in Ruby program.
e. Line break or no line break output are different reserved word (puts, print) in Ruby.
Reference:
Ruby Tutorial with Code Samples (n.d.), http://www.fincher.org/tips/Languages/Ruby/
Selina D’S. (n.d.), T New Product Development with Ruby on Rails, Retrieve 10 April 2009 from www.aspiresys.com/WhitePapers/whitepaper_new_product_development-RoR_paper.pdf
w3school (2009), JavaScript If...Else Statements, Retrieve 10 April 2009 from http://www.w3schools.com/JS/js_if_else.asp
Workshop 2: Model View Controller design appraoch
To do:
1. Setup a focus group (like a study group for peer learning) to work on the Ruby on Rails workshops via Interact tools as a class.
A focus group was set for to work on Ruby on Rails workshops at http://ltang18.blogspot.com
I also joined the focus group by Dennis at http://railsfocusgroup.blogspot.com/
2. What is meant by "convention over configuration" and how does it reduce coding?
3. Further work on understanding MVC:
a. See the wiki at http://wiki.rubyonrails.org/rails/pages/UnderstandingMVC
The content does not available!
b. Do the MVC tutorial at http://wiki.squeak.org/squeak/1767
The file MVCTutorial.zip is downloaded and studied.
Challenge Problems:
1. How is Rails structured to follow the MVC pattern?
Model (ActiveRecord ) :
The relationship between Object and Database is maintained by Model. It also handles validation, association and transactions. The tables in the database is binded with the ActiveRecord library inside the Model. It interfaces Ruby program code and table to manipulates database records.
View ( ActionView )
The format for data presentation which is controlled by the controller and usually integrated with AJAX technology.
When connection to Rail application, the embedded Ruby based system inside the ActionView library set templates for displaying data as a view.
Controller ( ActionController ):
Querying models and oranizing the data for different views are handled by controller.
The ActionController inside the controller breaks the data for ActiveRecord (the database interface) and ActionView (the presentation engine). (tutorialspoint.com)

to be continued.
Figure 1. Rails Framework (tutorialspoint.com)
In Rails, the folder structure seperate the model, controller and view as follows:

Figure 2. Rails folder structure to follow the MVC pattern
2. Apply the MVC design approach to our Project: Online Taxi Booking System.

Figure 3. Interface for managing rails applications
Online Taxi Booking System application skeleton is created by applying command:
rails OTBS

Figure 4. The folder structre after applying command in rails_apps folder.
Reference:
tutorialspoint.com (n.d.), Ruby on Rails Framework, Retrieved 12 April 2009 from http://www.tutorialspoint.com/cgi-bin/printversion.cgi?tutorial=ruby-on-rails&file=rails-framework.htm
tutorialspoint.com (n.d.), Ruby on Rails Framework, Retrieved 12 April 2009 from http://www.tutorialspoint.com/ruby-on-rails/rails-framework.htm
RailsGuiders (n.d.), Getting Started with Rails, Retrieved 12 April 2009 from http://guides.rubyonrails.org/getting_started.html
1. Setup a focus group (like a study group for peer learning) to work on the Ruby on Rails workshops via Interact tools as a class.
A focus group was set for to work on Ruby on Rails workshops at http://ltang18.blogspot.com
I also joined the focus group by Dennis at http://railsfocusgroup.blogspot.com/
2. What is meant by "convention over configuration" and how does it reduce coding?
3. Further work on understanding MVC:
a. See the wiki at http://wiki.rubyonrails.org/rails/pages/UnderstandingMVC
The content does not available!
b. Do the MVC tutorial at http://wiki.squeak.org/squeak/1767
The file MVCTutorial.zip is downloaded and studied.
Challenge Problems:
1. How is Rails structured to follow the MVC pattern?
Model (ActiveRecord ) :
The relationship between Object and Database is maintained by Model. It also handles validation, association and transactions. The tables in the database is binded with the ActiveRecord library inside the Model. It interfaces Ruby program code and table to manipulates database records.
View ( ActionView )
The format for data presentation which is controlled by the controller and usually integrated with AJAX technology.
When connection to Rail application, the embedded Ruby based system inside the ActionView library set templates for displaying data as a view.
Controller ( ActionController ):
Querying models and oranizing the data for different views are handled by controller.
The ActionController inside the controller breaks the data for ActiveRecord (the database interface) and ActionView (the presentation engine). (tutorialspoint.com)

to be continued.
Figure 1. Rails Framework (tutorialspoint.com)
In Rails, the folder structure seperate the model, controller and view as follows:

Figure 2. Rails folder structure to follow the MVC pattern
2. Apply the MVC design approach to our Project: Online Taxi Booking System.

Figure 3. Interface for managing rails applications
Online Taxi Booking System application skeleton is created by applying command:
rails OTBS

Figure 4. The folder structre after applying command in rails_apps folder.
Reference:
tutorialspoint.com (n.d.), Ruby on Rails Framework, Retrieved 12 April 2009 from http://www.tutorialspoint.com/cgi-bin/printversion.cgi?tutorial=ruby-on-rails&file=rails-framework.htm
tutorialspoint.com (n.d.), Ruby on Rails Framework, Retrieved 12 April 2009 from http://www.tutorialspoint.com/ruby-on-rails/rails-framework.htm
RailsGuiders (n.d.), Getting Started with Rails, Retrieved 12 April 2009 from http://guides.rubyonrails.org/getting_started.html
Workshop 1: Setting up the model railway
The Project
a. Login MySQL, create database and passenger_origin

b. Structure of the passenger_origin

c. Create table passenger_destination and list structure

To do:
1. I have subscribed the www.buildingwebapps.com for Learning Rails.
2. I have downloaded and installed the Ruby, RubyGems and Rails from www.rubyonrails.org

Figure 1. Screen Capture of the www.rubyonrails.org
3. Due to the portability of the RoR, I have chosen to use the pre-packaged solutions - Instant Rails for Windows platform instead of the install version of the RoR.
Challlenge Problems:
1. Make a list of all programming languages and Web development tools used by you in prior experiences. describe what you know about Web application frameworks before we begins.
Languages: VisualBASIC, VB.NET, C++, HTML, ASP, ASP.NET
The web application framework I knew is that It is a 2-tier based web application.
The first layer is the web interface interact with the users and the other layer is a server side application where the business logic and database systems are on the server(s).
2. Ruby is "an interpreted scripting language" for quick and easy object-oriented programming". Find out about the Ruby language and discover what this means.
Ruby is a language created by a Japanese - Yukihiro Matsumoto (matz). It is a object-oriented progarmming language with syntax like Perl and Smalltalk. Ruby is named because pearl is the birthstone for the month June and Ruby is the birthstone is July that means Ruby is powerful and as a successor of Perl language. (Wikipedia)
3. What is Rails and how does it work with Ruby?
Rails is a framework for programming web applications. It is developed with Ruby language. With its "Don't Repeat yourself (DRY)" philosohy, Rails allowing the developer to program less code for web application development. (Wikipedia)
4. What is meant by "convertion over configuration" in regards to the use of Rails in Web application development?
The convertion over configuration means the system applies assumption to the components to reduce the developer to change the settings that not involved with the web application. This reduces the developer to tweaking the unconventional parts of the application and architecture. (Jeremy)
5. When did Model-View-Controller begin and where is it used?
The Model-View-Controller (MVC) begins in 1978. It was used to support the
user's mental model to provide information for user checking and editing with its editor. (Trygve)
6. Describe the steps involved with the MVC design approach.
In Model-View-Controller design pattern, the web application is splitted into three seperate parts - Model, View and Controller.
Model is used to handle data and logic where the representation of the data for business are handled.
The View is used to handle the output to users. It retrieves information from model to output for users.
The Controller is used to hand input from users. The input can effect to the model and/or view in order to response to user input.
The relationship of the MVC and it structure is shown as follow:

Figure 2. Model-View-Controller pattern (java.sun.com 2002)
Reference:
About Ruby, Retrived 12 April 2009 from http://www.ruby-lang.org/en/about/
Wikipedia (n.d.), Ruby (programming language), Retrived 12 April 2009 from http://en.wikipedia.org/wiki/Ruby_(programming_language)
Improving designs with the MVC design pattern (2004), Retrived 12 April 2009 from http://java.sun.com/developer/EJTechTips/2004/tt0324.html
Java BluePrints: Model-View-Controller (2002), Retrived 12 April 2009 from http://java.sun.com/blueprints/patterns/MVC-detailed.html
Trygve, M. H. R. (n.d.), MVC XEROX PARC 1978-79, Retrived 12 April 2009 from http://heim.ifi.uio.no/~trygver/themes/mvc/mvc-index.html
Jeremy M. (February 2009), Patterns in Practice: Convention Over Configuration, Retrived 12 April 2009 from http://msdn.microsoft.com/en-us/magazine/dd419655.aspx
a. Login MySQL, create database and passenger_origin

b. Structure of the passenger_origin

c. Create table passenger_destination and list structure

To do:
1. I have subscribed the www.buildingwebapps.com for Learning Rails.
2. I have downloaded and installed the Ruby, RubyGems and Rails from www.rubyonrails.org

Figure 1. Screen Capture of the www.rubyonrails.org
3. Due to the portability of the RoR, I have chosen to use the pre-packaged solutions - Instant Rails for Windows platform instead of the install version of the RoR.
Challlenge Problems:
1. Make a list of all programming languages and Web development tools used by you in prior experiences. describe what you know about Web application frameworks before we begins.
Languages: VisualBASIC, VB.NET, C++, HTML, ASP, ASP.NET
The web application framework I knew is that It is a 2-tier based web application.
The first layer is the web interface interact with the users and the other layer is a server side application where the business logic and database systems are on the server(s).
2. Ruby is "an interpreted scripting language" for quick and easy object-oriented programming". Find out about the Ruby language and discover what this means.
Ruby is a language created by a Japanese - Yukihiro Matsumoto (matz). It is a object-oriented progarmming language with syntax like Perl and Smalltalk. Ruby is named because pearl is the birthstone for the month June and Ruby is the birthstone is July that means Ruby is powerful and as a successor of Perl language. (Wikipedia)
3. What is Rails and how does it work with Ruby?
Rails is a framework for programming web applications. It is developed with Ruby language. With its "Don't Repeat yourself (DRY)" philosohy, Rails allowing the developer to program less code for web application development. (Wikipedia)
4. What is meant by "convertion over configuration" in regards to the use of Rails in Web application development?
The convertion over configuration means the system applies assumption to the components to reduce the developer to change the settings that not involved with the web application. This reduces the developer to tweaking the unconventional parts of the application and architecture. (Jeremy)
5. When did Model-View-Controller begin and where is it used?
The Model-View-Controller (MVC) begins in 1978. It was used to support the
user's mental model to provide information for user checking and editing with its editor. (Trygve)
6. Describe the steps involved with the MVC design approach.
In Model-View-Controller design pattern, the web application is splitted into three seperate parts - Model, View and Controller.
Model is used to handle data and logic where the representation of the data for business are handled.
The View is used to handle the output to users. It retrieves information from model to output for users.
The Controller is used to hand input from users. The input can effect to the model and/or view in order to response to user input.
The relationship of the MVC and it structure is shown as follow:

Figure 2. Model-View-Controller pattern (java.sun.com 2002)
Reference:
About Ruby, Retrived 12 April 2009 from http://www.ruby-lang.org/en/about/
Wikipedia (n.d.), Ruby (programming language), Retrived 12 April 2009 from http://en.wikipedia.org/wiki/Ruby_(programming_language)
Improving designs with the MVC design pattern (2004), Retrived 12 April 2009 from http://java.sun.com/developer/EJTechTips/2004/tt0324.html
Java BluePrints: Model-View-Controller (2002), Retrived 12 April 2009 from http://java.sun.com/blueprints/patterns/MVC-detailed.html
Trygve, M. H. R. (n.d.), MVC XEROX PARC 1978-79, Retrived 12 April 2009 from http://heim.ifi.uio.no/~trygver/themes/mvc/mvc-index.html
Jeremy M. (February 2009), Patterns in Practice: Convention Over Configuration, Retrived 12 April 2009 from http://msdn.microsoft.com/en-us/magazine/dd419655.aspx
Subscribe to:
Comments (Atom)


