Saturday, November 14, 2009
The new starting point.
I am happy to share that I have finished the course. This blog site will stop from updating. Don't worry, I will create the other blog site soon to share other things that may be interesting.
Wednesday, May 27, 2009
Evaluation Report 2
Audio file is uploaded to EAST
Evaluation Report (Audio) also can be accessed with Sky Drive:
http://cid-df4d3bf95db02d9e.skydrive.live.com/self.aspx/.Public/A2.mp3
Script of the Evaluation Report:
I am Raymond TANG. I worked as a technical support in educational field, the exercises and workshops broader my view on latest programming approach and current technologies on business and e-commerce.
I heard the Enterprise Resource Planning (ERP) system but not the Customer Relationship Management (CRM) system and Supply Chain Management (SCM) system. This is a new experience for me know more about them.
The most interesting part of the exercise is the security part. For example, I knew cookies in browser can be collected by advertiser for sending junk email, but I don’t know the actual mechanism. With the exercise, I realized the way the cookies work on the advertiser.
Before workshops, I know the way to write a program, two tiers, three tiers, but not considering about the framework. Ruby on Rails provided me a chance, not only to learn the way to write a program, but also creating the MVC approach framework.
To sum up, no matter it is B2B or B2C, e-commerce is around us. Security is the most concerned topic between the e-commerce, to provide a safe and convenience way for planning, communicating, delivering, merchandising and purchasing.
Evaluation Report (Audio) also can be accessed with Sky Drive:
http://cid-df4d3bf95db02d9e.skydrive.live.com/self.aspx/.Public/A2.mp3
Script of the Evaluation Report:
I am Raymond TANG. I worked as a technical support in educational field, the exercises and workshops broader my view on latest programming approach and current technologies on business and e-commerce.
I heard the Enterprise Resource Planning (ERP) system but not the Customer Relationship Management (CRM) system and Supply Chain Management (SCM) system. This is a new experience for me know more about them.
The most interesting part of the exercise is the security part. For example, I knew cookies in browser can be collected by advertiser for sending junk email, but I don’t know the actual mechanism. With the exercise, I realized the way the cookies work on the advertiser.
Before workshops, I know the way to write a program, two tiers, three tiers, but not considering about the framework. Ruby on Rails provided me a chance, not only to learn the way to write a program, but also creating the MVC approach framework.
To sum up, no matter it is B2B or B2C, e-commerce is around us. Security is the most concerned topic between the e-commerce, to provide a safe and convenience way for planning, communicating, delivering, merchandising and purchasing.
My Computer is down again. >_<
My computer suddenly cannot startup after I press the switch yesterday morning.
I just become crazy because all the information including study guides, ebooks, the project files are stored in that hard drive.
The system is found to be certified (dead). Bad Luck.
I just become crazy because all the information including study guides, ebooks, the project files are stored in that hard drive.
The system is found to be certified (dead). Bad Luck.
Tuesday, May 19, 2009
Workshop 8: Evaluation and Report
1. List what you consider to be the three strengths of Ruby on Rails workshop series
a. Learn a new programming language for e-commerce
b. Learn the new kind of framework on software development
c. Practical the RoR skill on the workshops
2. List what you consider to be the three weaknesses of Ruby on Rails workshop series:
a. RoR version changes with its language, it is difficult to follow up.
b. Setup and configure the server will be difficult if no experience.
c. Difficult to classify if we should do both the “To do:” and “Challenge Problem:” or only “To do:”
3. List what aspects of Ruby on Rails workshop series that you found to be most difficult.
a.. Install and configure the server in the UNIX/Linux environment, it is not allowed in my workplace.
b. Instead of the text mode, if a GUI IDE introduced for RoR may improve the work for workshops.
c. The AJAX (not encounted before)
d. Lots of time used in the workshop
e. The work including exercises and workshops were too much for the part time student.
4. List what improvements could be made to the Ruby on Rails workshop series:
a. Introduce the GUI IDE.
b. Clear clarify if we should work on both "To do:" and “Challenge Problem:” or else.
Free response and reflective questions:
5. The MVC framework separates three type of work at place. It is found to be effective framework for development.
6. No. It is because the RoR can give me challenges and fulfillment.
7. No further comments
a. Learn a new programming language for e-commerce
b. Learn the new kind of framework on software development
c. Practical the RoR skill on the workshops
2. List what you consider to be the three weaknesses of Ruby on Rails workshop series:
a. RoR version changes with its language, it is difficult to follow up.
b. Setup and configure the server will be difficult if no experience.
c. Difficult to classify if we should do both the “To do:” and “Challenge Problem:” or only “To do:”
3. List what aspects of Ruby on Rails workshop series that you found to be most difficult.
a.. Install and configure the server in the UNIX/Linux environment, it is not allowed in my workplace.
b. Instead of the text mode, if a GUI IDE introduced for RoR may improve the work for workshops.
c. The AJAX (not encounted before)
d. Lots of time used in the workshop
e. The work including exercises and workshops were too much for the part time student.
4. List what improvements could be made to the Ruby on Rails workshop series:
a. Introduce the GUI IDE.
b. Clear clarify if we should work on both "To do:" and “Challenge Problem:” or else.
Free response and reflective questions:
5. The MVC framework separates three type of work at place. It is found to be effective framework for development.
6. No. It is because the RoR can give me challenges and fulfillment.
7. No further comments
Workshop 7: DEVELOPER’S THREAD (RED team)
Workshop 7
I would like to choose the UNIX platform to deploy the system. I have been using the Linux platform to provide service as production server such as Webmail, FTP in my workplace for years. The stability and the performance of the system are excellent. In terms of the system maintenance, the patch or fix packages release rapidly when bugs were found. Absolutely, it is important that it is free.
I would like to use the Mongrel and Mongrel cluster for deployment. In my experience in the workshop with InstantRails, it is a easy to use plugins to the RoR. Furthermore, Mongrel is a single-threaded application (Wikipedia 2009), with the management of the Mongrel with Mongrel-cluster plugins, the load of the system will be balanced on production server.
Microsoft platforms and development platform like JAVA and JRuby are not considered. Although it is more easy to configure the system with Microsoft platforms, the stability is not as well as UNIX for deployment as production server. JAVA and JRuby are not choosen. Although JAVA or JRuby can provide cross platform capability, but the performance of the system may not to be as good as just using the Apache with Mongrel. The other reason is that WiFi are popular, people can use their PDA phones or Smartphone to go Internet and browse the website directly deploying JAVA like platform may lead a slow performance on the client side.
Reference:
Wikipedia (2009), Mongrel (web server), Retrieved 27 May 2009 form http://en.wikipedia.org/wiki/Mongrel_(web_server)
Debian (n.d.), Mongrel plugin to manage a cluster of Mongrel servers, Retrieved 27 May 2009 from http://packages.debian.org/zh-cn/squeeze/mongrel-cluster
I would like to choose the UNIX platform to deploy the system. I have been using the Linux platform to provide service as production server such as Webmail, FTP in my workplace for years. The stability and the performance of the system are excellent. In terms of the system maintenance, the patch or fix packages release rapidly when bugs were found. Absolutely, it is important that it is free.
I would like to use the Mongrel and Mongrel cluster for deployment. In my experience in the workshop with InstantRails, it is a easy to use plugins to the RoR. Furthermore, Mongrel is a single-threaded application (Wikipedia 2009), with the management of the Mongrel with Mongrel-cluster plugins, the load of the system will be balanced on production server.
Microsoft platforms and development platform like JAVA and JRuby are not considered. Although it is more easy to configure the system with Microsoft platforms, the stability is not as well as UNIX for deployment as production server. JAVA and JRuby are not choosen. Although JAVA or JRuby can provide cross platform capability, but the performance of the system may not to be as good as just using the Apache with Mongrel. The other reason is that WiFi are popular, people can use their PDA phones or Smartphone to go Internet and browse the website directly deploying JAVA like platform may lead a slow performance on the client side.
Reference:
Wikipedia (2009), Mongrel (web server), Retrieved 27 May 2009 form http://en.wikipedia.org/wiki/Mongrel_(web_server)
Debian (n.d.), Mongrel plugin to manage a cluster of Mongrel servers, Retrieved 27 May 2009 from http://packages.debian.org/zh-cn/squeeze/mongrel-cluster
Workshop 6: Enjoying the Ride: Web framework alternatives, scalability and flexibility

Figure 1. Generate the site
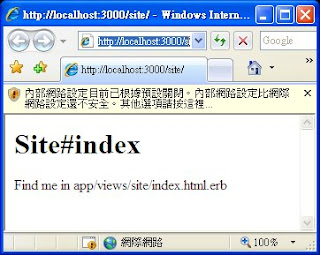
Figure 2. Result of site generation

Figure 3. Change the route

Figure 4. Welcome screen
At this stage, the file index.html in public folder is removed, the file index.erb in OTBS\app\views\site removed.

Figure 5. Screen after added link at the top of page

Figure 6. Screen after implementation of CSS

Figure 7. Change MySQL password and create database

Figure 8. Database structure at MySQL administrator

Figure 9. Register screen
Due to my computer system failure, it is required to rebuild the stuffs from scratch.
As the time constraint, the rebuild of the workshop was unsuccessful. I will do my best to try it again even passed the deadline of assessment.
I do not have any experience on writing AJAX program. According to the Wikipedia (2009), with the AJAX, the data exchange asynchronously between browser and server, the performance is much faster than always connected. The AJAX programming avoiding page reloads, that part of the screen is refreshed as it required. The load of the server reduced.
Reference:
Wikipedia (2009), Ajax (programming), Retrieved 27 May 2009 from http://en.wikipedia.org/wiki/Ajax_(programming)
Workshop 5: Admiring the scenery Forms, AJAX screen layout and mobile interfaces
I am joining the RED TEAM - DEVELOPER. It is because like to create programs, from concept to product.
Part A
1. Create the Rails application framework in the projects folder:

2. Running the application on localhost:3000 using the WeBrick ruby server (or Mongrel as alternative) and access via Web browser at http://localhost:3000/



3. Create the controller to make the application do an action. This is under the controller-action/model-view structure.


Result from browser

5. Create an action by editing and saving the mammal_controller.rb class in projects\animals\app\controllers using your text editor to add the method
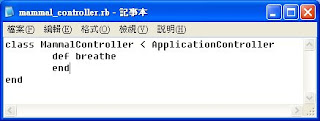
6. Start the WEBrick server and browse at http://localhost:3000/mammals/breathe where you will get a “missing template” message since it is missing a view for the breathe method.

7. Create and save a view in that directory by using a text editor to create a view called breathe.rhtml

Result from browser

8. Try Ruby code and HTML in the action view by using the <%....%> wrapper around the inserted Ruby code. Here are some snippets to try from workshop 4:

Result from browser

Part B
1. Create a new application called scenery in the same projects directory to demonstrate the use of an active view.

2. Create a controller called Demo in scenery\app\controllers
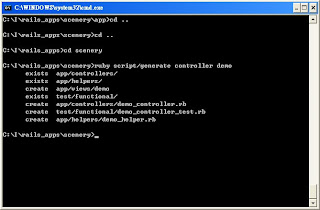
3. Add an action to demo_controller.rb as the method called rubycode


4. Add a view template - scenery\app\views\demo\rubycode.rhtml


Result at browser

8. Then modify and save the corresponding view template

9. Restart the Web server and navigate the browser

Part C
1. Create a new application called cabs in the same projects directory to demonstrate the use of an active view.

2. Create a controller called Vehicle in cabs\app\controllers

3. Add an action to vehicle_controller.rb as the method called cabtype

View result

6. Create a file in the public directory - \cabs\public called input.html

7. Edit the vehicle_controller.rb here is a start. The data in each form element in the Rails application can be accessed via its name and a hash called params

8. Edit the view template cabtype.rhtml

9. Start the Web server and go to the opening page of this application at http://localhost:3000/input.html

Result

10. Submit form data. What do you find?
I found error in the program. The if statement can not progress with the (=) equal to symbol when using boolean type of variable.
After fix the webpage and link. The information pass from webpage and to the controller vehicle_controller.rb and to the result page - cabtype.rhtml for output.
11. Report your progress or findings in your Developers Blog.
The select list use array. It is because the selection from user is the index value but not the text itself. So, the array is used to collect the text back from the index value.
Part A
1. Create the Rails application framework in the projects folder:

2. Running the application on localhost:3000 using the WeBrick ruby server (or Mongrel as alternative) and access via Web browser at http://localhost:3000/



3. Create the controller to make the application do an action. This is under the controller-action/model-view structure.


Result from browser

5. Create an action by editing and saving the mammal_controller.rb class in projects\animals\app\controllers using your text editor to add the method

6. Start the WEBrick server and browse at http://localhost:3000/mammals/breathe where you will get a “missing template” message since it is missing a view for the breathe method.

7. Create and save a view in that directory by using a text editor to create a view called breathe.rhtml

Result from browser

8. Try Ruby code and HTML in the action view by using the <%....%> wrapper around the inserted Ruby code. Here are some snippets to try from workshop 4:

Result from browser

Part B
1. Create a new application called scenery in the same projects directory to demonstrate the use of an active view.

2. Create a controller called Demo in scenery\app\controllers

3. Add an action to demo_controller.rb as the method called rubycode


4. Add a view template - scenery\app\views\demo\rubycode.rhtml


Result at browser

8. Then modify and save the corresponding view template

9. Restart the Web server and navigate the browser

Part C
1. Create a new application called cabs in the same projects directory to demonstrate the use of an active view.

2. Create a controller called Vehicle in cabs\app\controllers

3. Add an action to vehicle_controller.rb as the method called cabtype

View result

6. Create a file in the public directory - \cabs\public called input.html

7. Edit the vehicle_controller.rb here is a start. The data in each form element in the Rails application can be accessed via its name and a hash called params

8. Edit the view template cabtype.rhtml

9. Start the Web server and go to the opening page of this application at http://localhost:3000/input.html

Result

10. Submit form data. What do you find?
I found error in the program. The if statement can not progress with the (=) equal to symbol when using boolean type of variable.
After fix the webpage and link. The information pass from webpage and to the controller vehicle_controller.rb and to the result page - cabtype.rhtml for output.
11. Report your progress or findings in your Developers Blog.
The select list use array. It is because the selection from user is the index value but not the text itself. So, the array is used to collect the text back from the index value.
Monday, May 11, 2009
Exercise 26: End of the Line: Systems integration
I choose the Business process analysis.
2. Business process analysis
Organisations can use several systems to monitor, record business process transactions such as:
•Enterprise Resource Planning (ERP),
•Customer Relationship Management (CRM)
•Workflow Management,
These software systems store data on instances of business processes transactions and can be analysed using data or process mining (PM) and reverse business engineering (RBE). In the case of ERP systems, integration of all data and processes goes into a single database as system components – the ultimate integration notion, perhaps.
Summary:
I chose business process analysis and scattered bits together. According to the Sagebusiness.com (2008), "ERP systems for functions such as managing receivables, inventory, and finance, and CRM systems are used to manage contact relationships, cross-sells, and up-sells."
Although ERP and CRM are different systems, Sagebussiness.com (2008) stated that properly integration of the system increase the profitability and productivity than investment and efforts involved.
George (2008) suggested the following points for the system integrations:
1. Take a business process view of ERP-CRM integration
He suggested considering the benefit to the business than the individual business.
2. Determine how ERP-CRM integration can benefit end users
He suggested the users should gain improvement on experience the new integrated system.
3. Reduce fears around loss of control
He suggested that integration should reduce the duplication of the customer information.
4. Cultivating the right ERP-CRM integration team
According to the organization size, the integration team should be from different department with limited number of people to reduce conflicts.
5. Assigning process ownership for an ERP-CRM integration project
Due to the system is different in ERP and CRM, the new system should allow to manage different kind of data. The integration can be into single or multi instances strategies.
I don’t work on the ERP and CRM. As I studied the passages of system integration on both systems, when a relation of the planning of the resource to the customer needs, the "order-to-cash processes" (Sagebusiness.com 2008) leads the reduction of the cost. On the other hand, as the CRM can analysis for the market trend, the ERP can allocate more resources to the market that expanding for more profits.
Reference:
Walia S. (2008), CRM and E-Commerce: The Integration Payoff, Retrieved 25 May 2009 from http://www.crmbuyer.com/story/64103.html?wlc=1243405763
Sagebusiness.com.au (2008), ERP & CRM Integration Tips, Retrieved 25 May 2009 from http://www.sagebusiness.com.au/pg-news-erp-crm-software-integration-top-tips.seo
George L. (2008), Benefits of ERP-CRM integration, Retrieved 25 May 2009 from http://searchcrm.techtarget.com/generic/0,295582,sid11_gci1320412,00.html
2. Business process analysis
Organisations can use several systems to monitor, record business process transactions such as:
•Enterprise Resource Planning (ERP),
•Customer Relationship Management (CRM)
•Workflow Management,
These software systems store data on instances of business processes transactions and can be analysed using data or process mining (PM) and reverse business engineering (RBE). In the case of ERP systems, integration of all data and processes goes into a single database as system components – the ultimate integration notion, perhaps.
Summary:
I chose business process analysis and scattered bits together. According to the Sagebusiness.com (2008), "ERP systems for functions such as managing receivables, inventory, and finance, and CRM systems are used to manage contact relationships, cross-sells, and up-sells."
Although ERP and CRM are different systems, Sagebussiness.com (2008) stated that properly integration of the system increase the profitability and productivity than investment and efforts involved.
George (2008) suggested the following points for the system integrations:
1. Take a business process view of ERP-CRM integration
He suggested considering the benefit to the business than the individual business.
2. Determine how ERP-CRM integration can benefit end users
He suggested the users should gain improvement on experience the new integrated system.
3. Reduce fears around loss of control
He suggested that integration should reduce the duplication of the customer information.
4. Cultivating the right ERP-CRM integration team
According to the organization size, the integration team should be from different department with limited number of people to reduce conflicts.
5. Assigning process ownership for an ERP-CRM integration project
Due to the system is different in ERP and CRM, the new system should allow to manage different kind of data. The integration can be into single or multi instances strategies.
I don’t work on the ERP and CRM. As I studied the passages of system integration on both systems, when a relation of the planning of the resource to the customer needs, the "order-to-cash processes" (Sagebusiness.com 2008) leads the reduction of the cost. On the other hand, as the CRM can analysis for the market trend, the ERP can allocate more resources to the market that expanding for more profits.
Reference:
Walia S. (2008), CRM and E-Commerce: The Integration Payoff, Retrieved 25 May 2009 from http://www.crmbuyer.com/story/64103.html?wlc=1243405763
Sagebusiness.com.au (2008), ERP & CRM Integration Tips, Retrieved 25 May 2009 from http://www.sagebusiness.com.au/pg-news-erp-crm-software-integration-top-tips.seo
George L. (2008), Benefits of ERP-CRM integration, Retrieved 25 May 2009 from http://searchcrm.techtarget.com/generic/0,295582,sid11_gci1320412,00.html
Exercise 24: Virtual business worlds and cyberagents
1. Differentiate the various type of software agents
According to Ince (2004), There are eleven type of software agents and described as follows:
a. Chatterbots
converses with the user in some restricted form of natural language.
b. Commerce agents
In B2B environment, this agents process invoices, checking arrival of material for process, notifying the product arrival and create financial information.
c. Data management agents
Associated with corpora of data that processing text on web site into a summary.
d. Government agents
Used to search for government regulations or extracting government statistics.
e. News agents
Display the breaking news.
Search for specified news by user.
email the news story to user.
Personalize the newspaper according to users' preference.
f. Newsgroup agents
Sorting out, prioritise and display the posting according to the users keywords.
Search the FAQ list for answers to a specified question. Notify the user of the new information is discussed in newsgroup.
g. Shopping agents
Carry out tasks associated with the accessing of retail sites. It is used to compare prices on the retails sites and auction sites on the internet for the products.
h. Software agents
Carry out tasks associated with software
e.g. Notify for software update
i. Stock agents
Associated with the purchasing and selling stocks and shares.
j. Update agents
Notify the user when a change has occured which is of significance to the user
2. Describe how techniques such as artificial intellgence and statistical techniques are used in software agents.
Fuzzy agents is a kind of artificial intellgence which implements fuzzy logic. This agent uses a rule based system to deal and make decision with the conditions it adopt. (Wikipedia 2009)
In statistical techniques, the software agents uses data mining algorithms to analyse the rules and common behaviours from the information rich environments.
3. Identify various activities in e-commerce where software agents are curently in use.
According to Clurman, W., Foley, T., Guttman, R., Kupres, K. (1997), the following activities are currently in use.
i. Personalization
This is the sense in which it is literally an “agent” taking action in the interests of another just as a real estate agent is understood to represent the interests of a buyer or seller. The outcome of the agent’s primary task is controlled by specific information supplied by the user, the agent is personalized for that user.
ii. Brokering
Brokering is different from personalization in that brokering is the function of information retrieval and delivery, given personalized instructions. Again, the search engine that delivers query results is a simple example of a broker, as it gathers and delivers results based on personalized input. So-called “meta-indexes” perform this function on more than one data source.
iii. Negotiation
Negotiating agents may be empowered to execute transactions on behalf their users. The “program-trading” accepting and reviewing information supplied by the activity of an agent and determine the user threshold to make buying or selling decisions financial markets.
4. Computing ethics and bot programming case study: rocky
a.
An account username: train1 and password: train1 is obtained.

Figure 1. Login Screen

Figure 2. After login

Figure 3. Starting the bot

Figure 4. Normal Option
In the screen of normal option, the bot does not seems to know anything and does not response to the user typing. It always says "I don't understand that."

Figure 5. Say Option
In the screen with say option, the bot response, but it usually give uncertain or unexpect answer or asking unexpected questions.

Figure 6. emote Option
In the screen with emote option, the bot response, the response is much better especially on the postive and negative matter and illness . It still give some uncertain or unexpect answer or asking unexpected questions. When the answer from user is short. Sometimes it gives no response at all.

Figure 7. Stop the Rocky
c.
Accroding to Wikipedia (15 May 2009), ELIZA was a computer program of primitive natural language processing. It uses simple pattern matching techniques to response to its users.
As I chatted with the Rocky about, the Rocky is trying to match the pattern for postiive and negative attitude of the users. It seems not response the long and complex sentance well.
Reference:
Nwana H. S. (1996), Software Agents: An Overview, Retrieved 13 May 2009 from http://www.sce.carleton.ca/netmanage/docs/AgentsOverview/ao.html
Wikipedia (2009), ELIZA, Retrieved 18 May 2009 from http://en.wikipedia.org/wiki/ELIZA
Grossklags J., Schmidt C. (2003), Artificial Software Agents on Thin Double Auction Markets - A Human Trader Experiment, Retrieved 15 May 2009 from http://www.sfb504.uni-mannheim.de/~cschmidt/paper/IAT2003-grossklags-schmidt.pdf
Wroclaw (2007), Using Data Mining Algorithms for Statistical Learning of a Software Agent, Retrieved 17 May 2009 from http://portal.acm.org/citation.cfm?id=1482853
Zhang S., Hu Q., Wang D. (2007), Application of Software Agent to e-Commerce Consumer Buying Support, Retrieved 18 May 2009 from http://ieeexplore.ieee.org/Xplore/login.jsp?url=http%3A%2F%2Fieeexplore.ieee.org%2Fiel5%2F4318334%2F4318335%2F04318860.pdf%3Farnumber%3D4318860&authDecision=-203
Clurman, W., Foley, T., Guttman, R., Kupres, K. (1997), Electronic Commerce with Software Agents, Retrieved 18 May 2009 from http://alumni.media.mit.edu/~guttman/research/commerce/papers/commerce.pdf
xxxxxx OLD ANSWER for Question 3 xxxxxx
i. Supporting
a. Consumer Buying Support
According to Zhang, Hu and Wang (2007), "Facing the flood of information and increasing competitive environment, the e-Commerce seller must make its software facility more customer-oriented, more intelligent, and build one-to-one marketing. A new e-Commerce model is presented to support consumer buying decision making."
b. Health Care Support
Moreno, A., Nealon, J. L. (n.d.) stated that "software agents technology is being applied in very diverse problems in health care, ranging from community care to management of organ transplants."
xxxxxx END xxxxxx
According to Ince (2004), There are eleven type of software agents and described as follows:
a. Chatterbots
converses with the user in some restricted form of natural language.
b. Commerce agents
In B2B environment, this agents process invoices, checking arrival of material for process, notifying the product arrival and create financial information.
c. Data management agents
Associated with corpora of data that processing text on web site into a summary.
d. Government agents
Used to search for government regulations or extracting government statistics.
e. News agents
Display the breaking news.
Search for specified news by user.
email the news story to user.
Personalize the newspaper according to users' preference.
f. Newsgroup agents
Sorting out, prioritise and display the posting according to the users keywords.
Search the FAQ list for answers to a specified question. Notify the user of the new information is discussed in newsgroup.
g. Shopping agents
Carry out tasks associated with the accessing of retail sites. It is used to compare prices on the retails sites and auction sites on the internet for the products.
h. Software agents
Carry out tasks associated with software
e.g. Notify for software update
i. Stock agents
Associated with the purchasing and selling stocks and shares.
j. Update agents
Notify the user when a change has occured which is of significance to the user
2. Describe how techniques such as artificial intellgence and statistical techniques are used in software agents.
Fuzzy agents is a kind of artificial intellgence which implements fuzzy logic. This agent uses a rule based system to deal and make decision with the conditions it adopt. (Wikipedia 2009)
In statistical techniques, the software agents uses data mining algorithms to analyse the rules and common behaviours from the information rich environments.
3. Identify various activities in e-commerce where software agents are curently in use.
According to Clurman, W., Foley, T., Guttman, R., Kupres, K. (1997), the following activities are currently in use.
i. Personalization
This is the sense in which it is literally an “agent” taking action in the interests of another just as a real estate agent is understood to represent the interests of a buyer or seller. The outcome of the agent’s primary task is controlled by specific information supplied by the user, the agent is personalized for that user.
ii. Brokering
Brokering is different from personalization in that brokering is the function of information retrieval and delivery, given personalized instructions. Again, the search engine that delivers query results is a simple example of a broker, as it gathers and delivers results based on personalized input. So-called “meta-indexes” perform this function on more than one data source.
iii. Negotiation
Negotiating agents may be empowered to execute transactions on behalf their users. The “program-trading” accepting and reviewing information supplied by the activity of an agent and determine the user threshold to make buying or selling decisions financial markets.
4. Computing ethics and bot programming case study: rocky
a.
An account username: train1 and password: train1 is obtained.

Figure 1. Login Screen

Figure 2. After login

Figure 3. Starting the bot

Figure 4. Normal Option
In the screen of normal option, the bot does not seems to know anything and does not response to the user typing. It always says "I don't understand that."

Figure 5. Say Option
In the screen with say option, the bot response, but it usually give uncertain or unexpect answer or asking unexpected questions.

Figure 6. emote Option
In the screen with emote option, the bot response, the response is much better especially on the postive and negative matter and illness . It still give some uncertain or unexpect answer or asking unexpected questions. When the answer from user is short. Sometimes it gives no response at all.

Figure 7. Stop the Rocky
c.
Accroding to Wikipedia (15 May 2009), ELIZA was a computer program of primitive natural language processing. It uses simple pattern matching techniques to response to its users.
As I chatted with the Rocky about, the Rocky is trying to match the pattern for postiive and negative attitude of the users. It seems not response the long and complex sentance well.
Reference:
Nwana H. S. (1996), Software Agents: An Overview, Retrieved 13 May 2009 from http://www.sce.carleton.ca/netmanage/docs/AgentsOverview/ao.html
Wikipedia (2009), ELIZA, Retrieved 18 May 2009 from http://en.wikipedia.org/wiki/ELIZA
Grossklags J., Schmidt C. (2003), Artificial Software Agents on Thin Double Auction Markets - A Human Trader Experiment, Retrieved 15 May 2009 from http://www.sfb504.uni-mannheim.de/~cschmidt/paper/IAT2003-grossklags-schmidt.pdf
Wroclaw (2007), Using Data Mining Algorithms for Statistical Learning of a Software Agent, Retrieved 17 May 2009 from http://portal.acm.org/citation.cfm?id=1482853
Zhang S., Hu Q., Wang D. (2007), Application of Software Agent to e-Commerce Consumer Buying Support, Retrieved 18 May 2009 from http://ieeexplore.ieee.org/Xplore/login.jsp?url=http%3A%2F%2Fieeexplore.ieee.org%2Fiel5%2F4318334%2F4318335%2F04318860.pdf%3Farnumber%3D4318860&authDecision=-203
Clurman, W., Foley, T., Guttman, R., Kupres, K. (1997), Electronic Commerce with Software Agents, Retrieved 18 May 2009 from http://alumni.media.mit.edu/~guttman/research/commerce/papers/commerce.pdf
xxxxxx OLD ANSWER for Question 3 xxxxxx
i. Supporting
a. Consumer Buying Support
According to Zhang, Hu and Wang (2007), "Facing the flood of information and increasing competitive environment, the e-Commerce seller must make its software facility more customer-oriented, more intelligent, and build one-to-one marketing. A new e-Commerce model is presented to support consumer buying decision making."
b. Health Care Support
Moreno, A., Nealon, J. L. (n.d.) stated that "software agents technology is being applied in very diverse problems in health care, ranging from community care to management of organ transplants."
xxxxxx END xxxxxx
Exercise 25: M-commerce and the e-wallet and mobile devices
1. What is meant by a location based service?
When doing the e-commerce or m-commerce. The technologies tries to locate the region of the user stay and provide information on the product and shop nearby according to the user need.
For example, when typing the www.yahoo.com to the URL at browser, the system of Yahoo will redirect the user to the local website instead of the global or website of other countries.
When a user purchase a produce through e-commerce or m-commerce. The system will locate the shop nearby the user for product delivery instead of sending from the other countries. This promotes the speed of product delivery, reduce cost by reducing the transportation cost, increase customer satification by better local customer service.
When doing the e-commerce or m-commerce. The technologies tries to locate the region of the user stay and provide information on the product and shop nearby according to the user need.
For example, when typing the www.yahoo.com to the URL at browser, the system of Yahoo will redirect the user to the local website instead of the global or website of other countries.
When a user purchase a produce through e-commerce or m-commerce. The system will locate the shop nearby the user for product delivery instead of sending from the other countries. This promotes the speed of product delivery, reduce cost by reducing the transportation cost, increase customer satification by better local customer service.
Exercise 21: Shopping cart specifications
Develop the class diagram for the following shopping cart specifications:
A shoppingCart object is associated with only one creditCard and
customer and to items in itemToBuy object. Persistent customer
information such as name, billing address, delivery address, e-mail address
and credit rating is stored in the customer object. The credit card object is
associated with a frequentShopper discount object, if the credit rating
for the customer is good. The customer can make or cancel orders as well
as add and delete items to the shopping cart product. The credit card
object contains the secure method for checking that the charge is authentic.
Class Diagram for shopping cart

A shoppingCart object is associated with only one creditCard and
customer and to items in itemToBuy object. Persistent customer
information such as name, billing address, delivery address, e-mail address
and credit rating is stored in the customer object. The credit card object is
associated with a frequentShopper discount object, if the credit rating
for the customer is good. The customer can make or cancel orders as well
as add and delete items to the shopping cart product. The credit card
object contains the secure method for checking that the charge is authentic.
Class Diagram for shopping cart

Exercise 20: Modeling with UML
Use Case, Class, Sequence, Collaboration, State chart, Activity, Component and Deployment diagrams are used in UML. Describe each of the eight (8) main diagrams used in UML.
According to the Ambler (2007), the main diagrams used in UML are as following:
Use Case diagram
"Shows use cases, actors, and their interrelationships. "
Class diagram
"Shows a collection of static model elements such as classes and types, their contents, and their relationships. "
Sequence diagram
"Models the sequential logic, in effect the time ordering of messages between classifiers."
Collaboration diagram
"Shows instances of classes, their interrelationships, and the message flow between them. Communication diagrams typically focus on the structural organization of objects that send and receive messages. Formerly called a Collaboration Diagram."
State chart
"Describes the states an object or interaction may be in, as well as the transitions between states. Formerly referred to as a state diagram, state chart diagram, or a state-transition diagram."
Activity diagram
"Depicts high-level business processes, including data flow, or to model the logic of complex logic within a system."
Component diagram
"Depicts the components that compose an application, system, or enterprise. The components, their interrelationships, interactions, and their public interfaces are depicted."
Deployment diagram
"Shows the execution architecture of systems. This includes nodes, either hardware or software execution environments, as well as the middleware connecting them."
Reference:
Ambler, S. W. (2007), Introduction to the Diagrams of UML 2.0, Retrieved 20 May 2009 from http://www.agilemodeling.com/essays/umlDiagrams.htm
According to the Ambler (2007), the main diagrams used in UML are as following:
Use Case diagram
"Shows use cases, actors, and their interrelationships. "
Class diagram
"Shows a collection of static model elements such as classes and types, their contents, and their relationships. "
Sequence diagram
"Models the sequential logic, in effect the time ordering of messages between classifiers."
Collaboration diagram
"Shows instances of classes, their interrelationships, and the message flow between them. Communication diagrams typically focus on the structural organization of objects that send and receive messages. Formerly called a Collaboration Diagram."
State chart
"Describes the states an object or interaction may be in, as well as the transitions between states. Formerly referred to as a state diagram, state chart diagram, or a state-transition diagram."
Activity diagram
"Depicts high-level business processes, including data flow, or to model the logic of complex logic within a system."
Component diagram
"Depicts the components that compose an application, system, or enterprise. The components, their interrelationships, interactions, and their public interfaces are depicted."
Deployment diagram
"Shows the execution architecture of systems. This includes nodes, either hardware or software execution environments, as well as the middleware connecting them."
Reference:
Ambler, S. W. (2007), Introduction to the Diagrams of UML 2.0, Retrieved 20 May 2009 from http://www.agilemodeling.com/essays/umlDiagrams.htm
Exercise 22: Differentiate between software systems
Customer Relationship Management (CRM)
CRM is a strategy used to learn more about customers' needs and behaviors in order to develop stronger relationships with them
a. providing services and products that are exactly what your customers want
b. offering better customer service
c. cross selling products more effectively
d. helping sales staff close deals faster
e. retaining existing customers and discovering new ones
Supply Chain Management (SCM)
There are five major functions in Supply Chain Management software. Most of the companies requires only some component in their business, so the software for SCM is usually fragmented.
According to Wailgum (2007), the five components are:
a. Plan
i. planning is developing a set of metrics to monitor the supply chain so that it is efficient, costs less and delivers high quality and value to customers.
b. Source
i. develop a set of product pricing, delivery and payment processes with suppliers and create metrics for monitoring and improving the relationships
ii. processes for managing their goods and services inventory, including receiving and verifying shipments, transferring them to the manufacturing facilities and authorizing supplier payments.
c. Make
i. schedule the activities necessary for production, testing, packaging and preparation for delivery.
d. Deliver
i. coordinate the receipt of orders from customers, develop a network of warehouses, pick carriers to get products to customers and set up an invoicing system to receive payments.
e. Return
i. Supply chain planners have to create a responsive and flexible network for receiving defective and excess products back from their customers and supporting customers who have problems with delivered products.
Conclustion:
To sum up, both software performing different functions. CRM trends to collect information on customer behavor and habits for designing strategy for selling products while SCM trends to plan for the production, testing and delivery of the products.
Reference:
Wailgum T. (March 06, 2007), CRM Definition and Solutions, Retrieved 19 May 2009 from http://www.cio.com/article/40295/CRM_Definition_and_Solutions
Wailgum T. (March 19, 2007), Supply Chain Management Definition and Solutions, Retrieved 19 May 2009 from http://www.cio.com/article/40940/Supply_Chain_Management_Definition_and_Solutions
Business Link (2007), Customer relationship management, Retrieved 19 May 2009 from http://www.businesslink.gov.uk/bdotg/action/detail?r.l1=1073861197&r.l3=1075422922&r.lc=en&type=RESOURCES&itemId=1075422931&r.l2=1075422920&r.s=sc#
CRM is a strategy used to learn more about customers' needs and behaviors in order to develop stronger relationships with them
a. providing services and products that are exactly what your customers want
b. offering better customer service
c. cross selling products more effectively
d. helping sales staff close deals faster
e. retaining existing customers and discovering new ones
Supply Chain Management (SCM)
There are five major functions in Supply Chain Management software. Most of the companies requires only some component in their business, so the software for SCM is usually fragmented.
According to Wailgum (2007), the five components are:
a. Plan
i. planning is developing a set of metrics to monitor the supply chain so that it is efficient, costs less and delivers high quality and value to customers.
b. Source
i. develop a set of product pricing, delivery and payment processes with suppliers and create metrics for monitoring and improving the relationships
ii. processes for managing their goods and services inventory, including receiving and verifying shipments, transferring them to the manufacturing facilities and authorizing supplier payments.
c. Make
i. schedule the activities necessary for production, testing, packaging and preparation for delivery.
d. Deliver
i. coordinate the receipt of orders from customers, develop a network of warehouses, pick carriers to get products to customers and set up an invoicing system to receive payments.
e. Return
i. Supply chain planners have to create a responsive and flexible network for receiving defective and excess products back from their customers and supporting customers who have problems with delivered products.
Conclustion:
To sum up, both software performing different functions. CRM trends to collect information on customer behavor and habits for designing strategy for selling products while SCM trends to plan for the production, testing and delivery of the products.
Reference:
Wailgum T. (March 06, 2007), CRM Definition and Solutions, Retrieved 19 May 2009 from http://www.cio.com/article/40295/CRM_Definition_and_Solutions
Wailgum T. (March 19, 2007), Supply Chain Management Definition and Solutions, Retrieved 19 May 2009 from http://www.cio.com/article/40940/Supply_Chain_Management_Definition_and_Solutions
Business Link (2007), Customer relationship management, Retrieved 19 May 2009 from http://www.businesslink.gov.uk/bdotg/action/detail?r.l1=1073861197&r.l3=1075422922&r.lc=en&type=RESOURCES&itemId=1075422931&r.l2=1075422920&r.s=sc#
Exercise 23: Searching mechanisms
1. What is a spider? What does it do?
Schneider (2006) stated that spider is a part of the search engine. It is used to search the webpage and website which interesting to people automatically.
Awad (2004) defined that "spider: a software tool that prowls the internet looking for new sites where information is likely to reside."
During the search, the spider will collect information from the page such as the links contained on the page, keywords, title, content and also "meta" tag for user to search in the future.
2. What is a meta-search engine? Provide some examples.
meta is the keywords that describe the webpages but not part of the web content. (Schneider)
Rosen (2002) pointed that the meta-search engine looks for the meta tag in the webpages only. It then locates the website to the user by keyword matching.
Examples of meta-search engine:
Clusty
Dogpile
3. How can you get your site listed at major search sites; and how could you improve your site ranking?
a. Register a suitable domain name for the website.
b. Register the website to the major search engine.
c. Put the website into subitable category.
d. Use suitable meta in the website for spider to locate.
e. Better design and content of web to make it a popular search.
e. Paid or sponsor to the company of search engine to increase its rank.
f. Advertise on the search engine.
Reference:
Schneider, G. P. (2006), Electronic Commerce Sixth Annual Edition, Thomson, Canada, p. 203-205
Awad, E. M. (2004), Electronic Commerce (2nd ed), Pearson Education, NJ, p. 44
Rosen A. (2002), The e-commerce question and answer book: a survival guide for business managers (2nd ed), American Management Association, NY, p. 182
Meta-Search Engines, Retrieved 16 May 2009 from http://www.lib.berkeley.edu/TeachingLib/Guides/Internet/MetaSearch.html
Ince, D. (2004), Developing Distributed and E-commerce Applications (2nd ed.), Pearson, p. 438-439
Schneider (2006) stated that spider is a part of the search engine. It is used to search the webpage and website which interesting to people automatically.
Awad (2004) defined that "spider: a software tool that prowls the internet looking for new sites where information is likely to reside."
During the search, the spider will collect information from the page such as the links contained on the page, keywords, title, content and also "meta" tag for user to search in the future.
2. What is a meta-search engine? Provide some examples.
meta is the keywords that describe the webpages but not part of the web content. (Schneider)
Rosen (2002) pointed that the meta-search engine looks for the meta tag in the webpages only. It then locates the website to the user by keyword matching.
Examples of meta-search engine:
Clusty
Dogpile
3. How can you get your site listed at major search sites; and how could you improve your site ranking?
a. Register a suitable domain name for the website.
b. Register the website to the major search engine.
c. Put the website into subitable category.
d. Use suitable meta in the website for spider to locate.
e. Better design and content of web to make it a popular search.
e. Paid or sponsor to the company of search engine to increase its rank.
f. Advertise on the search engine.
Reference:
Schneider, G. P. (2006), Electronic Commerce Sixth Annual Edition, Thomson, Canada, p. 203-205
Awad, E. M. (2004), Electronic Commerce (2nd ed), Pearson Education, NJ, p. 44
Rosen A. (2002), The e-commerce question and answer book: a survival guide for business managers (2nd ed), American Management Association, NY, p. 182
Meta-Search Engines, Retrieved 16 May 2009 from http://www.lib.berkeley.edu/TeachingLib/Guides/Internet/MetaSearch.html
Ince, D. (2004), Developing Distributed and E-commerce Applications (2nd ed.), Pearson, p. 438-439
Exercise 19: TP monitors and transaction protocols
1. Give a description in your own words of the ACID proprtties of a transaction.
Atomicity (A)
Atomicity is used to ensure the transaction is successfully completed or not to prevent incomplete transactions.
In case of transaction success and completed. For example, the client paid for goods and the merchant is received his money.
In case of transaction failed and incomplete. For example, the client money remains in his account and the merchant do not receive any money.
Consistency (C)
When a transaction transforms from one state to another, intermediate points may be produced in database before the transaction commit and complete. Consistency is that the transaction does not require the intermediate points to transform from one state to another.
Isolation (I)
When there are concurrent transactions are running, the tranaction assigned to process should be complete and commit before another transaction to start process.
Durability (D)
The commited transaction should be availible at any time it is being used.
2. Describe a TP monitor environment. How can a TP monitor stop an operating system being overwhelmed?
The softwareag.com (2006) stated that the TP monitor environment contains user session data is referred to as thread. The session data used for the user session.
Figure 1. Environment of the TP monitor, Natural is a program running in the operating system (softwareag.com 2006)

As all administrative tasks of an operating system involving time must be created by TP monitor which is used to allocate the resources basis on the request each time such as process allocation and storage allocation. The load of the operating system is prevented from being overwhelmed. (Gray J., Reuter A., 1993)
3. What is difference in load balancing with traditional and transactional MOM, RPC and conversations?
In traditional RPC model, the request from user should be queued and wait synchronously for the server to execute and return the reply where the client and server should be free at the same time.
Messge-oriented middleware help to resolve the problem of the wait time. It acts as a middleware between the client and server, buffering the requests from user and replies from servers. As it runs in asynchronous model, it is no need to wait for client and server to be free at the same time.
In transactional MOM and RPC, the message queue is divided, distributed into queues and maintained at queue managers. The messages queues can be integrated for direct transaction processing and allow to commit or undone.
As a result, as the queue is divided, the load of the servers is then evenly distributed. (Mahmoud 2004)
4. Why is a two-phase commit protocol better than a one-phrase commit protocol?
The two-phrase commit protocol is better than one-phrase protocol. It is because the two phrase protocol confirm the transaction is received and recoverable before the transaction transofrm and commit. In case of the system fail, the transaction can be recovered or processed through the protocol. (Zurich)
Reference:
PCMAG.COM (n.d.), Definition of: TP monitor,Retrieved 14 May 2009 from http://www.pcmag.com/encyclopedia_term/0,2542,t=TP+monitor&i=53022,00.asp
PCMAG.COM (n.d.), Definition of: two-phase commit, Retrieved 14 May 2009 from http://www.pcmag.com/encyclopedia_term/0,2542,t=two-phase+commit&i=53281,00.asp
Zurich, ETH (n.d.), Message Oriented Middleware (MOM), Retrieved 15 May 2009 from http://www.iks.inf.ethz.ch/education/ws04/eai/Lecture-8.pdf
Zurich, ETH (n.d.), Message Oriented Middleware (MOM), Retrieved 15 May 2009 from http://www.iks.inf.ethz.ch/education/ws03/eai/Lecture-5.pdf
Kenneth M. A. (2006), http://www.cs.colorado.edu/~kena/classes/7818/f06/lectures/03/index.html
softwareag.com (2006), TP/OS Interface, Retrieved 15 May 2009 from https://cis.tamu.edu/systems/database/manuals/NAT421/arc/tp_mf_0040.htm
PCMAG.COM (2009), Definition of: TP monitor, Retrieved 15 May 2009 from http://www.pcmag.com/encyclopedia_term/0,2542,t=TP+monitor&i=53022,00.asp
Gray J., Reuter A. (1993), Transaction Processing: Concepts and Techniques, Morgan Kaufmann Publisher, p. 363
Mahmoud Q. H. (2004), Middleware for communications, John Wiley and Sons, p. 65-66
Atomicity (A)
Atomicity is used to ensure the transaction is successfully completed or not to prevent incomplete transactions.
In case of transaction success and completed. For example, the client paid for goods and the merchant is received his money.
In case of transaction failed and incomplete. For example, the client money remains in his account and the merchant do not receive any money.
Consistency (C)
When a transaction transforms from one state to another, intermediate points may be produced in database before the transaction commit and complete. Consistency is that the transaction does not require the intermediate points to transform from one state to another.
Isolation (I)
When there are concurrent transactions are running, the tranaction assigned to process should be complete and commit before another transaction to start process.
Durability (D)
The commited transaction should be availible at any time it is being used.
2. Describe a TP monitor environment. How can a TP monitor stop an operating system being overwhelmed?
The softwareag.com (2006) stated that the TP monitor environment contains user session data is referred to as thread. The session data used for the user session.
Figure 1. Environment of the TP monitor, Natural is a program running in the operating system (softwareag.com 2006)

As all administrative tasks of an operating system involving time must be created by TP monitor which is used to allocate the resources basis on the request each time such as process allocation and storage allocation. The load of the operating system is prevented from being overwhelmed. (Gray J., Reuter A., 1993)
3. What is difference in load balancing with traditional and transactional MOM, RPC and conversations?
In traditional RPC model, the request from user should be queued and wait synchronously for the server to execute and return the reply where the client and server should be free at the same time.
Messge-oriented middleware help to resolve the problem of the wait time. It acts as a middleware between the client and server, buffering the requests from user and replies from servers. As it runs in asynchronous model, it is no need to wait for client and server to be free at the same time.
In transactional MOM and RPC, the message queue is divided, distributed into queues and maintained at queue managers. The messages queues can be integrated for direct transaction processing and allow to commit or undone.
As a result, as the queue is divided, the load of the servers is then evenly distributed. (Mahmoud 2004)
4. Why is a two-phase commit protocol better than a one-phrase commit protocol?
The two-phrase commit protocol is better than one-phrase protocol. It is because the two phrase protocol confirm the transaction is received and recoverable before the transaction transofrm and commit. In case of the system fail, the transaction can be recovered or processed through the protocol. (Zurich)
Reference:
PCMAG.COM (n.d.), Definition of: TP monitor,Retrieved 14 May 2009 from http://www.pcmag.com/encyclopedia_term/0,2542,t=TP+monitor&i=53022,00.asp
PCMAG.COM (n.d.), Definition of: two-phase commit, Retrieved 14 May 2009 from http://www.pcmag.com/encyclopedia_term/0,2542,t=two-phase+commit&i=53281,00.asp
Zurich, ETH (n.d.), Message Oriented Middleware (MOM), Retrieved 15 May 2009 from http://www.iks.inf.ethz.ch/education/ws04/eai/Lecture-8.pdf
Zurich, ETH (n.d.), Message Oriented Middleware (MOM), Retrieved 15 May 2009 from http://www.iks.inf.ethz.ch/education/ws03/eai/Lecture-5.pdf
Kenneth M. A. (2006), http://www.cs.colorado.edu/~kena/classes/7818/f06/lectures/03/index.html
softwareag.com (2006), TP/OS Interface, Retrieved 15 May 2009 from https://cis.tamu.edu/systems/database/manuals/NAT421/arc/tp_mf_0040.htm
PCMAG.COM (2009), Definition of: TP monitor, Retrieved 15 May 2009 from http://www.pcmag.com/encyclopedia_term/0,2542,t=TP+monitor&i=53022,00.asp
Gray J., Reuter A. (1993), Transaction Processing: Concepts and Techniques, Morgan Kaufmann Publisher, p. 363
Mahmoud Q. H. (2004), Middleware for communications, John Wiley and Sons, p. 65-66
Exercise 18: Threading demostration in Python
Source Code of the threaddemo.py

Process Explain:
In this demo, the first part is defining the objects, variables and values.
The second part defining the common variable which will be access by the threads.
The third part is the major part of the threaddemo.
During the main program runs, the program acquire the lock for the the common variable and add a value into it. A delay of a random time is started just after the release of the common variable. At this moment, the other thread can be created by the main program. After the delay is end, the thread acquire the lock again and reduce the variable for the number of running processes.
Findings:
According to the result provided with the exercise, the longer the wait time o the thread, the later end of the process. This program favor the smaller program. The smaller thread uses the waiting time of the long waited thread to get its job done. Thread in this program simulate the multi-tasking environment to a common resources.

Process Explain:
In this demo, the first part is defining the objects, variables and values.
The second part defining the common variable which will be access by the threads.
The third part is the major part of the threaddemo.
During the main program runs, the program acquire the lock for the the common variable and add a value into it. A delay of a random time is started just after the release of the common variable. At this moment, the other thread can be created by the main program. After the delay is end, the thread acquire the lock again and reduce the variable for the number of running processes.
Findings:
According to the result provided with the exercise, the longer the wait time o the thread, the later end of the process. This program favor the smaller program. The smaller thread uses the waiting time of the long waited thread to get its job done. Thread in this program simulate the multi-tasking environment to a common resources.
Subscribe to:
Comments (Atom)


